Of course, mobile apps aren’t the only supply of privacy challenges. Any Website searching you need to do on your Laptop could possibly be logged and associated with you (and connected to your mobile Net browsing, for instance), and While compared desktop personal computers have a tendency to get a lot more privacy-protection choices, they’re rarely established as being the default. We've got some recommendations for browser extensions that can help.
The courtroom also pointed to your many years-previous rule called the “3rd-bash doctrine,” which retains that the government frequently doesn’t require a warrant to acquire information about an individual from a corporation or An additional 3rd party with whom she has “voluntarily” shared it.
It’s possible that your login credentials were compromised when your phone was hacked. When you’ve taken off the malware, reset all of your passwords and produce exceptional passwords for each account.
“This actually adds just one step concerning the provisioning of that use of the application,” he continues. “And as a result of way the user expertise has conditioned the acceptance of most prompts like a gate to accessing functionality, most people will just allow the application access to no matter what it is actually requesting. I think This can be some thing we are all responsible of eventually.”
Other occasions, the virus may well secretly transfer cash on the attacker’s accounts throughout the phone’s online banking application. “The most effective get rid of for these destructive apps is prevention,” notes Pargman. Steer clear of applications that assure no cost access to top quality content, aren’t stated in nicely-recognized application stores, and don’t Have a very record of assessments. These are the apps security experts would in no way have on their phone.
Delete apps you don’t use: Almost everyone has downloaded an app for an individual purpose then straight away forgotten about this. Just about every Occasionally, scroll by your listing of applications and delete something you no longer use or need to have.
Finding the operating system and community weaknesses in a corporation's technological know-how infrastructure.
The most important matter is to search for professional cell phone hackers for hire. Axilus On the net Company Ltd can help you shield your cell phone from external threats and continue to keep it hackproof so you can live in peace with none anxieties.
SAML authentication certificates, created with resources in addition to committed cloud identification solutions, can be forged by hackers, In keeping with a new evidence of principle.
According to the Bureau of Labor Stats, the cybersecurity industry will only keep on to grow in the coming yrs. Occupation projections for roles like cybersecurity analyst demonstrate a 33% boost in growth in excess of great site the subsequent few years.
Observe when services call for logins and try to find other choices: If you initial open up an app, some providers love to toss login screens before you using a teeny, tiny, virtually invisible X within the corner to say no. If an application seems to demand a login but doesn’t provide a valuable benefit for doing so—which include syncing your options concerning devices or to a website—take a look at the application to determine if You may use it without having building an account.
Take into account the applications you down load: Right before downloading any application, ask yourself regardless of whether you really need it. If it basically gives you entry to a support which you could use via a Website browser rather, heading With all the browser is a greater plan.
– Pentester27 Dec 22, 2019 at 0:forty nine As for @MechMK1's issue, there are actually diverse kinds of equipment to use. A phone is a good deal more functional to maneuver about in situations like wifi war driving or MITM to observe packets as it's in your pocket, or to setup a Social engineering Web-site operating on your phone wherever your phone is your server, as your phone is often on as opposed to your Computer system.
Android reset Recommendations differ by company. You ought to visit your phone maker’s Site for specific Recommendations. For most Android phones, you may access the reset selection via your Options menu, then navigate to “General Management” to reset your phone.
 Ralph Macchio Then & Now!
Ralph Macchio Then & Now!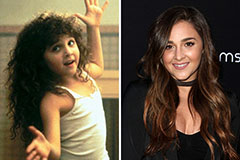 Alisan Porter Then & Now!
Alisan Porter Then & Now! Amanda Bearse Then & Now!
Amanda Bearse Then & Now! Brandy Then & Now!
Brandy Then & Now! Michelle Trachtenberg Then & Now!
Michelle Trachtenberg Then & Now!